IAM Clients
Overview
An IAM client is defined as an application, such as a game server or website, that requests access to protected platform resources. IAM clients allow you to control which resources can be accessed by an application, as opposed to a specific user.
IAM clients implement the OAuth 2.0 framework. You may have used other OAuth clients in the past, such as when using your GMail or Facebook account to log in to websites.
IAM clients can be defined under the publisher or game namespace, depending on whether the intended application is specific to one of your games or used by all games on your platform.
Client Types
There are two client types, as per the OAuth 2.0 Client Type framework:
- A confidential client requires a combination of Client ID and Client Secret to authorize with the backend. Confidential clients are normally needed in cases where you do not want to log in with a user account (such as a game server), and as a result, will typically have access permissions defined on the client itself. Therefore, confidential clients should only be used in cases where you can control who has access to the client's ID and secret, to prevent unauthorized users from being able to access your services.
- A public client does not specify a client secret; only the client ID is needed for authorization. Public clients are best for applications that require a user to log in with their user account. Permissions should generally not be defined for public clients, since the user's permissions will override the client's permissions once the user is signed into their account.
Common IAM Clients
Most projects typically define a few common client archetypes:
- Game client IAM client for game clients should be configured as public. It should have no permissions assigned, because the permissions will come from the signed-in user.
- Game server hosted by Armada IAM client for dedicated servers should also be configured as public, but you will need to assign permissions to the client if your dedicated servers do not login as a user (the most common case). For an example of permissions that would typically be assigned to a dedicated server IAM client, see the example permissions below.
- Dedicated Server Uploader IAM client for uploading dedicated server builds. Since access for uploaders is usually tightly controlled, it is best to specify these types of clients as confidential.
- Launcher IAM clients for the launcher should be configured as a public client. Once the user signs in, that user's permissions will override the launcher client permissions. But the launcher client will need to be given permissions to access certain services on its own, such as the login service.
Fields
Client ID serves as the unique ID for the client across the system. It is automatically generated when you first create the client.
Client Type defines how secure the client's login tokens will be. You can choose between Public and Confidential types. Refer to the Client Types section to read more about this.
Secret serves as the password for confidential clients. You can fill the field manually, or have the system create one for you by clicking the Generate Client Secret button.
NOTE
Once the client has been created, you can no longer access the client secret. Make sure you save the secret in a secure place.
Client Name serves as the name of the client, and is how this client will be identified in user-facing forms and documents.
Namespace defines which namespace this client should be created within. This only affects where the client appears in the Admin Portal, and does not necessarily affect what resources the client can access.
Platform defines which third-party platforms the SDK client runs on. This field is optional. If you choose not to bind to any third-party platform, input None.
Base URI is only needed for clients that are used by services, and should be set to the URI of the service itself. For clients that are not intended to be used to allow a service to access the rest of the platform, the value should be empty.
Target Audience is used to constrain which service endpoints the client is allowed to access. When given a value, it serves as a white list to allow backend services to quickly reject connection attempts before client or user permissions are checked.
When a client attempts to access a service endpoint, the service first checks the client's Target Audience list. The connection attempt will be rejected if the service's URI does not match the Base URI of any of the clients listed in the Target Audience field (unless the field is empty). If the client passes the Target Audience check (or if the client's Target Audience field is empty), the service proceeds to the next step in authenticating the client's request, such as checking permissions or scope.
The Target Audience drop down contains a list of clients (from the namespace that the client is defined in) along with the Base URI value specified by that client.
Redirect URI is only used by clients that represent web-based applications (such as a website or a launcher). For web-based clients, the value should be set to the URL that the user should be redirected to upon successful login. For other types of clients (game server, game client, server uploaders, etc.), although the RedirectURI is not used for anything, it is customary to input http://127.0.0.1, as this field must have a value for all clients.
Prerequisites
Permissions are used to grant access to specific resources within our services. Make sure your account has the following permissions before you attempt to manage IAM clients in the Admin Portal. For a full list of permissions that impact IAM clients management, see the IAM tab of the permissions reference.
| Permissions | Action | |
|---|---|---|
| Create a Client | ADMIN:NAMESPACE:{namespace}:CLIENT | Create |
| Retrieve Client | ADMIN:NAMESPACE:{namespace}:CLIENT | Update |
| Update Client | ADMIN:NAMESPACE:{namespace}:CLIENT | Update |
| Update Client Permission | ||
| Add Client Permission | ||
| Delete Client Permission | ADMIN:NAMESPACE:{namespace}:CLIENT | Delete |
Permissions work slightly differently depending on whether they are assigned to IAM Clients or Roles assigned to users. For more information, read the Authentication and Authorization documentation.
Manage Clients in the Admin Portal
Create a Client
In the Admin Portal, go to the Platform Configuration section and click the OAuth Clients menu.
On the OAuth Clients page, make sure that you are in the right namespace. Then, click Create New and fill out the appropriate fields (see the Fields section above for more information).
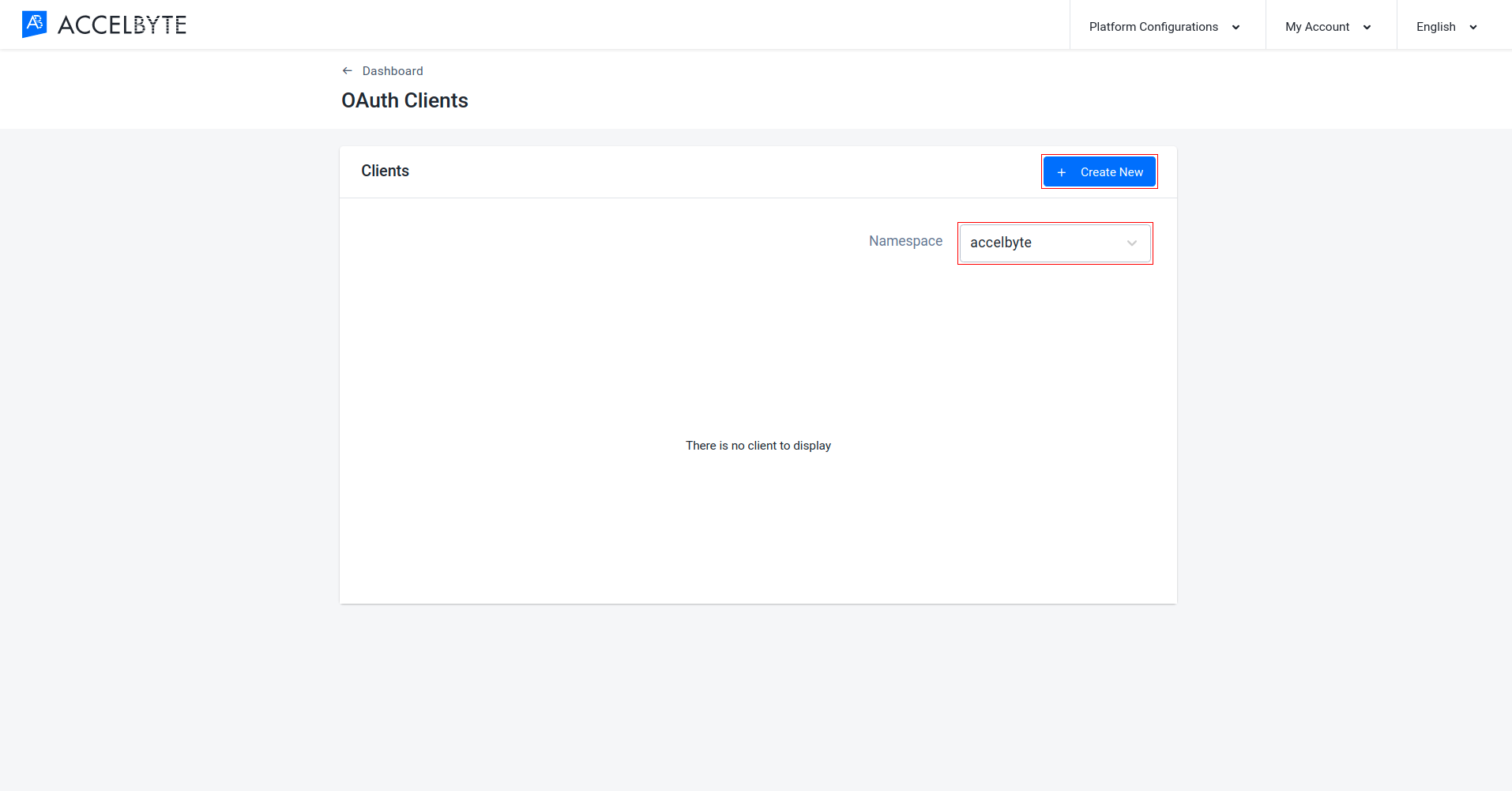
Once completed, click Create. The new IAM Client will be created.
Add Permissions to a Client
After you create a client, you can add permissions to the client by following the steps below.
In the Admin Portal, go to the Platform Configuration section and click the OAuth Clients menu.
Click View next to the client to which you want to add permissions.
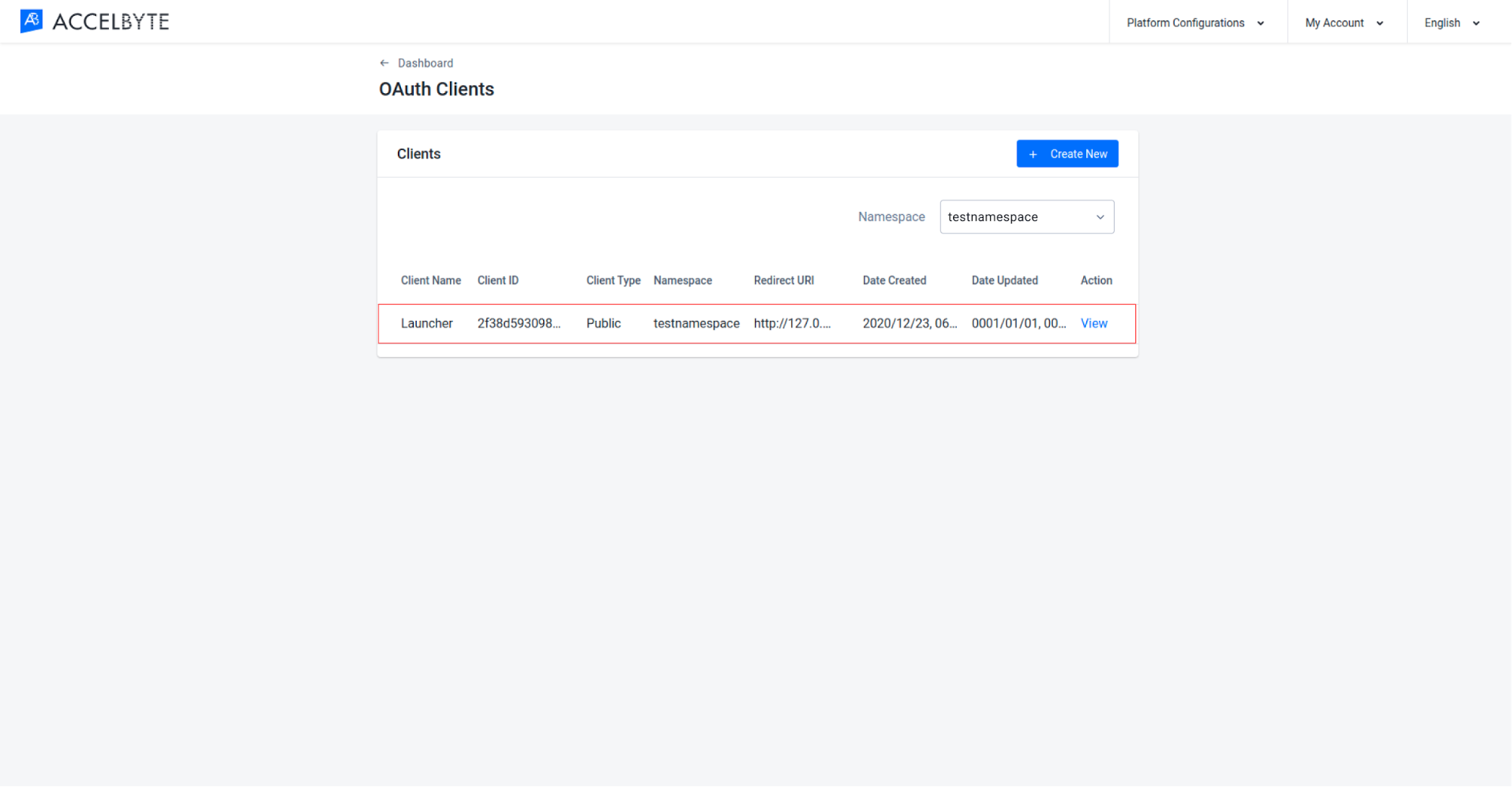
On the Client Details page, switch to the Permissions tab.
Click the Add button to add a new permission to the client.
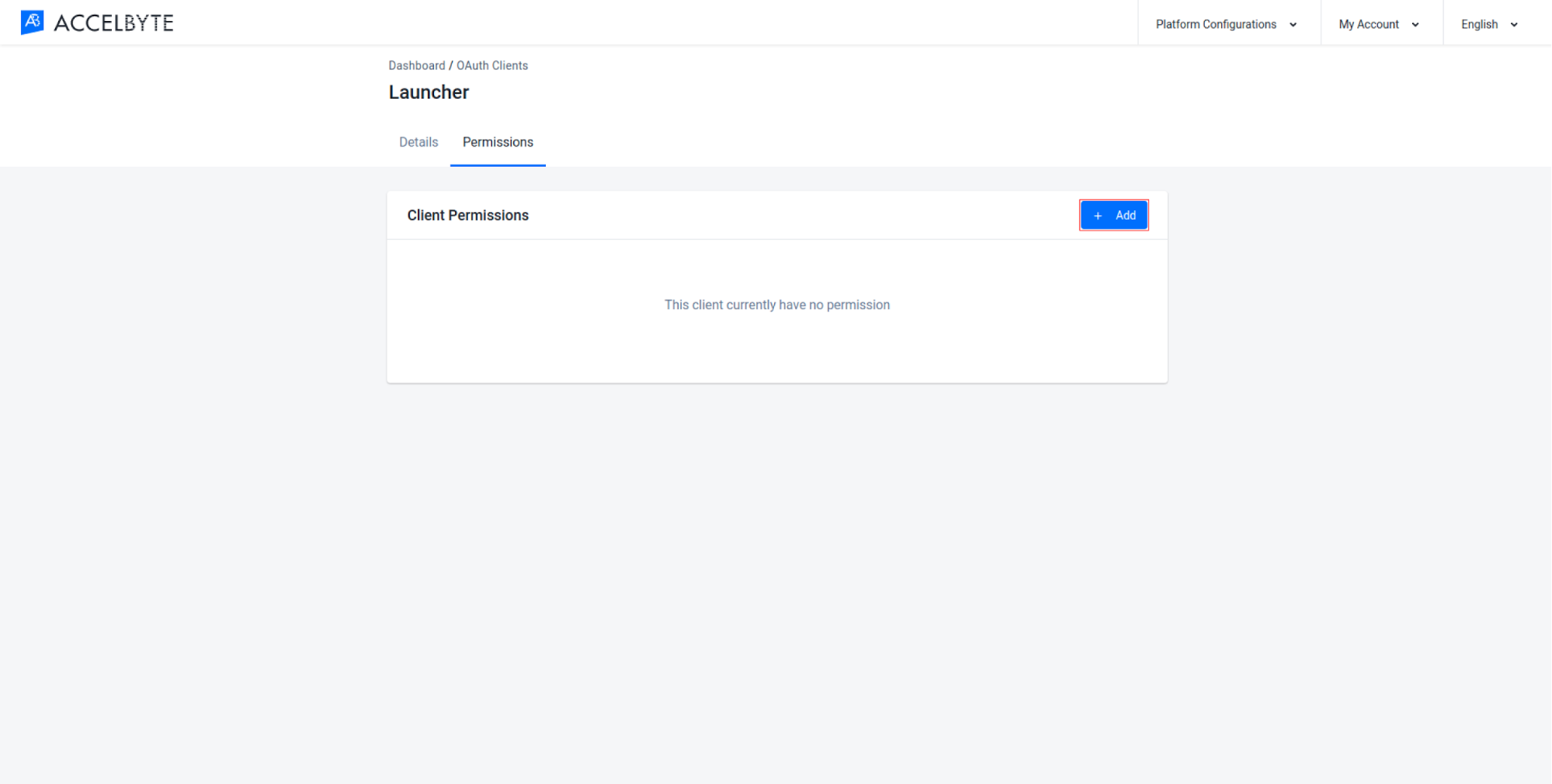
Fill in the required fields:
Enter a permission tag into the Resource field. A permission tag is a string containing multiple tokens that is used to grant access to specific resources. For more information, see the Permissions page or the permissions reference.
Select the action or actions the permission requires in the Action field. These are also listed in the Permissions Reference.
Here's a list of permissions required or frequently used by each common client type:
Dedicated Server Client (Mandatory)
| Permission | Action |
|---|---|
| ADMIN:DSM | READ |
| NAMESPACE:{namespace}:DSM:SERVER | UPDATE |
Dedicated Server Client (Optional)
You should give these permissions to a dedicated server client depending on the services you are using. See the permissions reference for more information about what these permissions do.
| Permission | Action |
|---|---|
| ADMIN:NAMESPACE:{namespace}:ENTITLEMENT | READ |
| ADMIN:NAMESPACE:{namespace}:PARTY:STORAGE | READ, UPDATE |
| ADMIN:NAMESPACE:{namespace}:STATITEM | UPDATE |
| ADMIN:NAMESPACE:{namespace}:USER:*:ACHIEVEMENT | UPDATE |
| ADMIN:NAMESPACE:{namespace}:USER:*:CLOUDSAVE:RECORD | CREATE, READ, UPDATE, DELETE |
| ADMIN:NAMESPACE:{namespace}:USER:*:ENTITLEMENT | READ |
| ADMIN:NAMESPACE:{namespace}:USER:*:PUBLIC:CLOUDSAVE:RECORD | CREATE, READ, UPDATE |
| ADMIN:NAMESPACE:{namespace}:USER:*:STATITEM | CREATE, READ, UPDATE |
| ADMIN:NAMESPACE:{namespace}:USER:*:WALLET | UPDATE |
| NAMESPACE:{namespace}:SESSION | CREATE, READ, UPDATE |
| ADMIN:NAMESPACE:{namespace}:MATCHMAKING:CHANNEL | CREATE, DELETE |
Dedicated Server Uploader Client (Mandatory)
| Permission | Action |
|---|---|
| NAMESPACE:{namespace}:DSUS:CONFIG | Create |
| NAMESPACE:{namespace}:DSUS:IMAGE | Create |
| NAMESPACE:{namespace}:DSUS:IMAGE | Read |
| NAMESPACE:{namespace}:DSM:SERVER | Create, Update |
| NAMESPACE:{namespace}:DSM:CONFIG | Read |
Once completed, the permission will appear in the client permission list.
Related Concepts
- Permissions are used to grant clients access to resources.